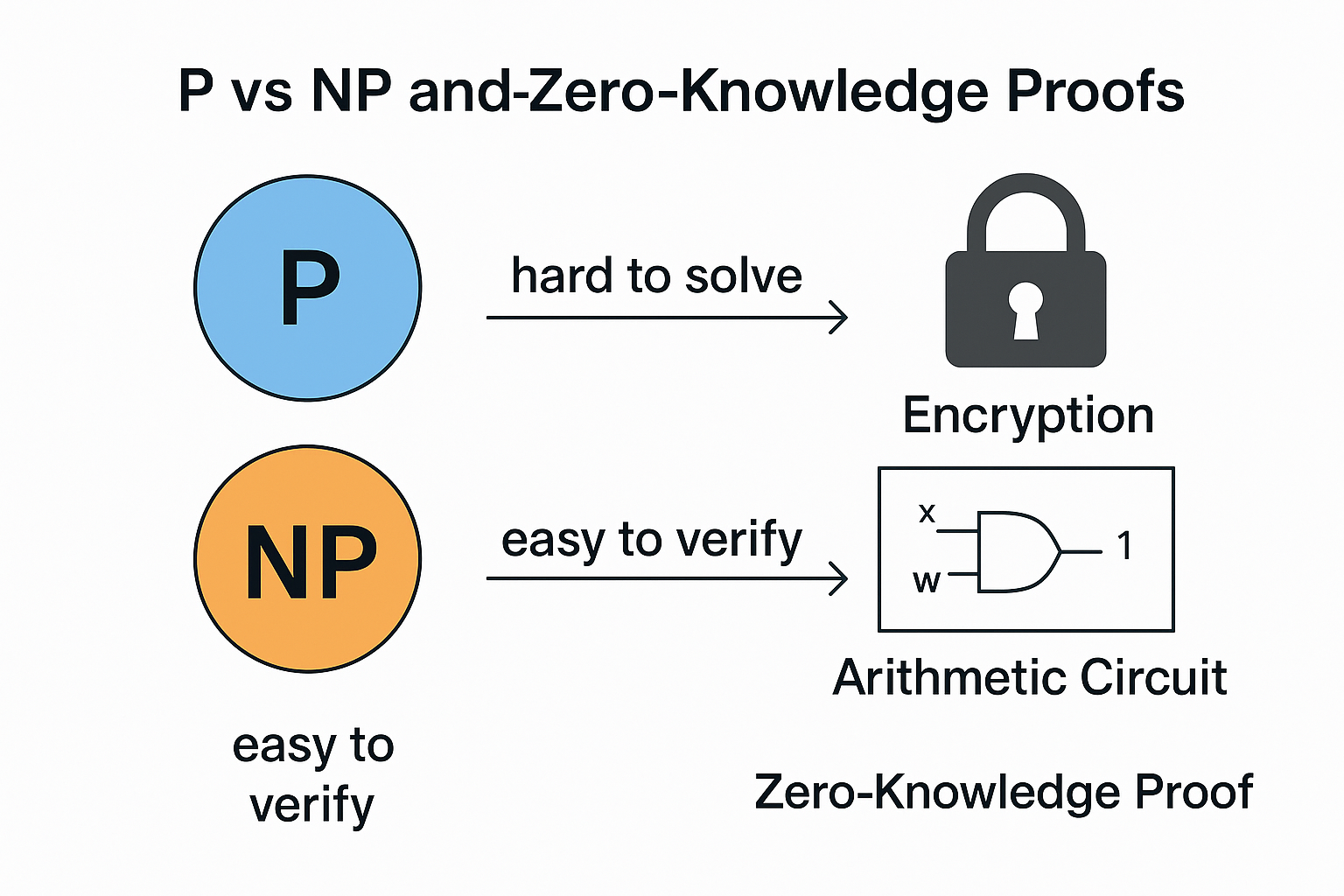
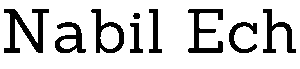Understanding Zero-Knowledge Proofs Through the Lens of P vs NP
1. Introduction — The Hidden Thread Between Math and Privacy If you’re reading this, chances are you’ve used encryption today — probably without realizing it. Every time you send a message, check your email, or make a blockchain transaction, your data is protected by math. But not just any math — it’s protected by problems […]
Understanding Zero-Knowledge Proofs Through the Lens of P vs NP Read More »